
如何修改Kubernetes的SSL证书有效期
主机配置规划
| 服务器名称(hostname) | 系统版本 | 配置 | 内网IP | 外网IP(模拟) |
|---|---|---|---|---|
| k8s-master | CentOS7.7 | 2C/4G/20G | 172.16.1.110 | 10.0.0.110 |
| k8s-node01 | CentOS7.7 | 2C/4G/20G | 172.16.1.111 | 10.0.0.111 |
| k8s-node02 | CentOS7.7 | 2C/4G/20G | 172.16.1.112 | 10.0.0.112 |
为什么要修改证书有效期
Kubernetes默认的证书有效期都是1年,因此需要我们每年都更新证书,显然这对我们实际生产环境来说是很不友好的;因此我们要对Kubernetes的SSL证书有效期进行修改。
证书有效期查看
1 | [root@k8s-master pki]# pwd |
由上可见,除了ca根证书,其他证书有效期都是1年。
证书有效时限修改
go环境部署
go语言中文网
1 | https://studygolang.com/ |
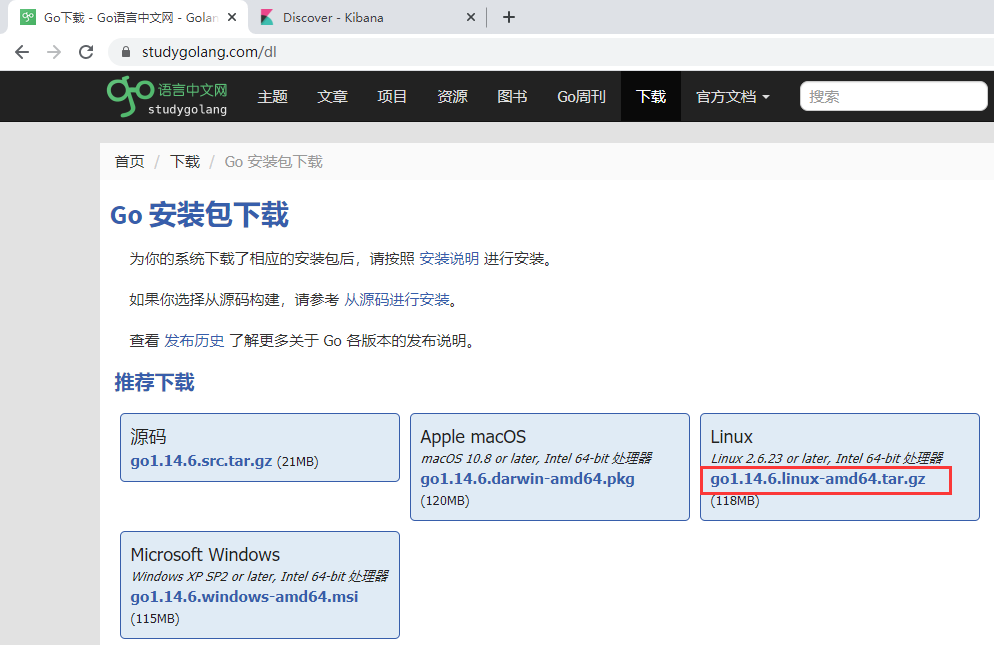
在Linux命令行下载
1 | [root@k8s-master software]# wget https://studygolang.com/dl/golang/go1.14.6.linux-amd64.tar.gz |
Kubernetes源码下载与更改证书策略
当期k8s版本
1 | [root@k8s-master software]# kubectl version |
根据k8s版本下载源码
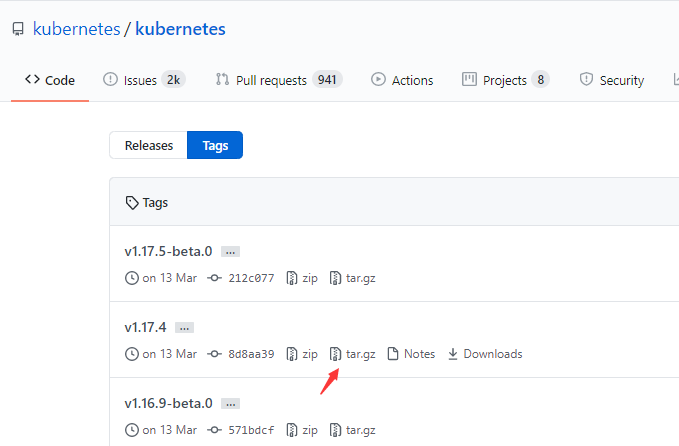
操作步骤
1 | [root@k8s-master software]# wget https://github.com/kubernetes/kubernetes/archive/v1.17.4.tar.gz |
更新kubeadm并备份原证书
1 | # kubeadm更新 |
证书更新
操作如下:
1 | # 证书更新 |
由上可见,除了CA根证书,其他证书有效期已经改为 100 年。
kubeadm-config.yaml文件参见如下
1 | [root@k8s-master k8s_install]# pwd |
相关阅读
1、基于kubeadm快速部署kubernetes K8S V1.17.4集群-无坑完整版
完毕!


